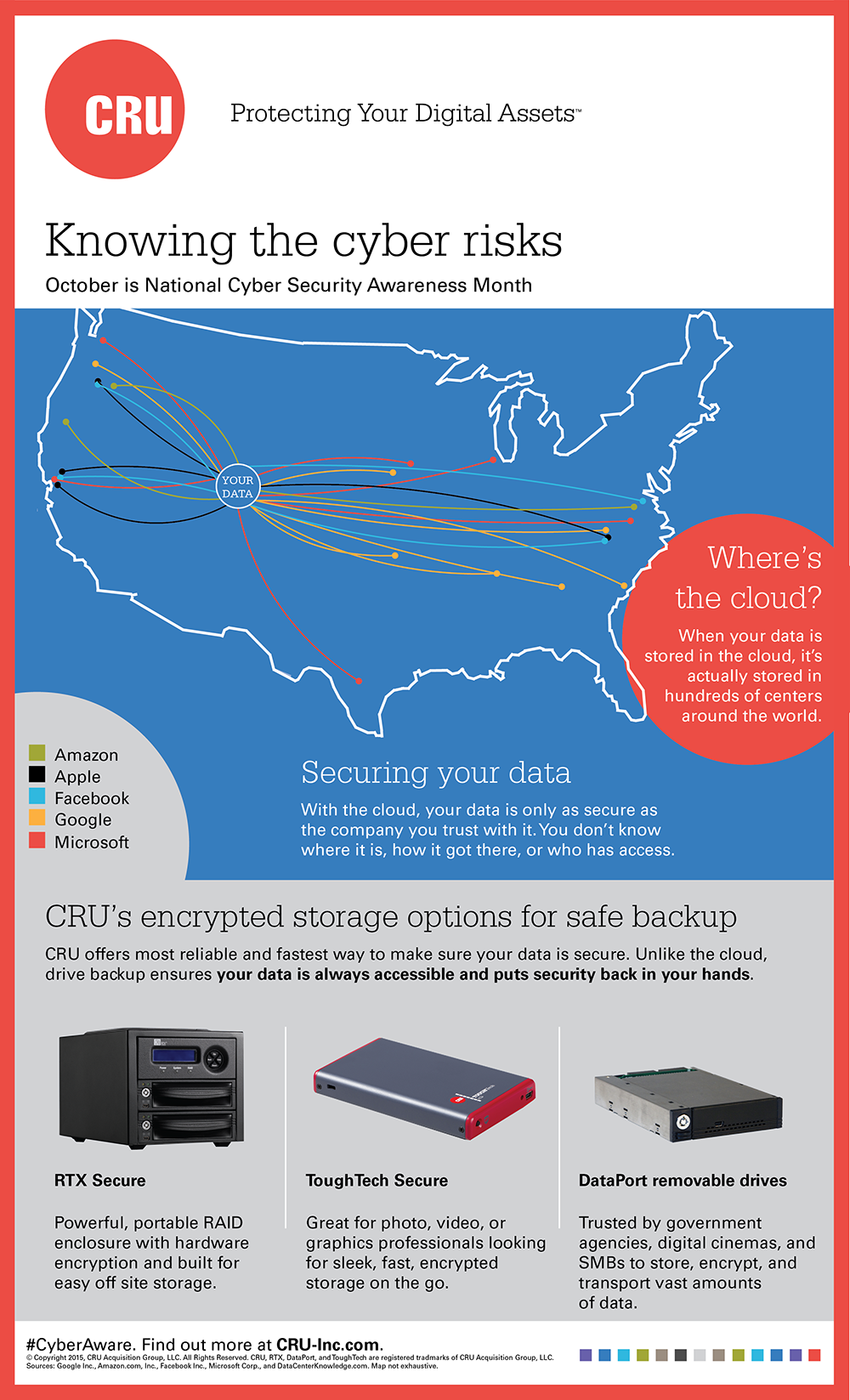
With the cloud, your data is only as secure as the company you trust with it. You don’t know where it is, how it got there, or who has access.
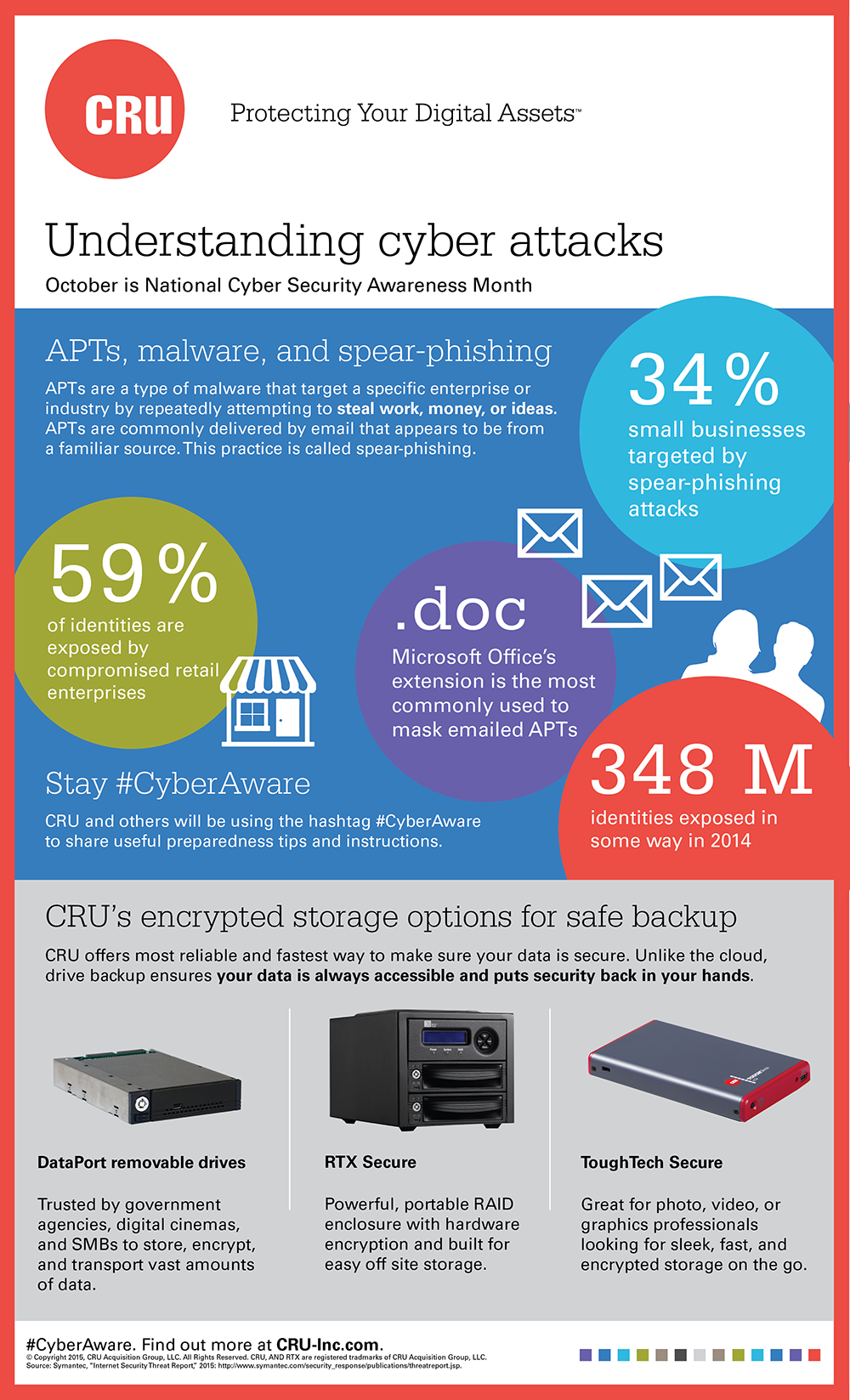
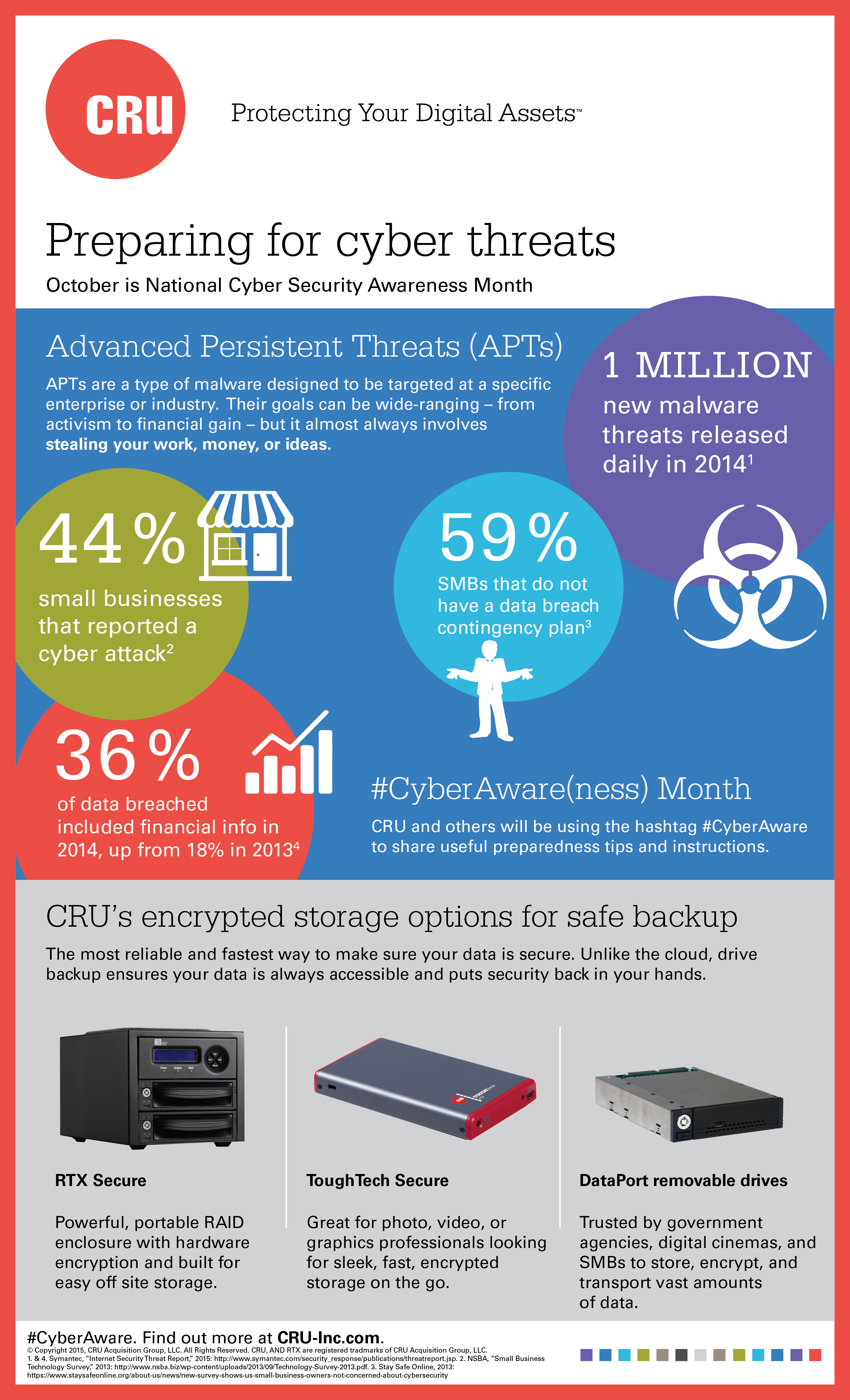
Continue reading →APTs are a type of malware that target a specific enterprise or industry by repeatedly attempting to steal work, money, or ideas. This malware is commonly delivered by email that appears to be from a familiar source. This practice is called spear phishing.
Continue reading →October is Cyber Security Awareness Month, and CRU is joining the conversation on social media and on our blog with preparedness tips and information that can help our customers combat the growing threat of cyber attack.
Continue reading →This post is a part of a six-part series from the white paper "The Measure of an Enclosure-Five Factors to Consider When Choosing External Data Storage". Can't wait to read the whole paper? You don't have to! Read it right here. The paper includes a glossary, charts and illustrations to help explain further.
Continue reading →This post is a part of a six-part series from the white paper "The Measure of an Enclosure-Five Factors to Consider When Choosing External Data Storage". Can't wait to read the whole paper? You don't have to! Read it right here. The paper includes a glossary, charts and illustrations to help explain further.
Continue reading →This post is a part of a six-part series from the white paper "The Measure of an Enclosure-Five Factors to Consider When Choosing External Data Storage". Can't wait to read the whole paper? You don't have to! Read it right here. The paper includes a glossary, charts and illustrations to help explain further.
Continue reading →This post is a part of a six-part series from the white paper "The Measure of an Enclosure-Five Factors to Consider When Choosing External Data Storage". Can't wait to read the whole paper? You don't have to! Read it right here. The paper includes a glossary, charts and illustrations to help explain further.
Continue reading →